In this 21st century, threats evolve fast. What is penetration testing? This question matters. Penetration testing (or “pentesting”) simulates real attacks. It reveals hidden vulnerabilities before bad actors exploit them. Every business—from startups to enterprises—faces constant risk. Understanding penetration testing empowers decision-makers to protect assets, maintain trust, and meet compliance.
What is Penetration Testing? Key Types for Your Business
What is penetration testing? At its core, it’s an authorized cyberattack simulation. Skilled ethical hackers probe systems, applications, and networks. They mimic real-world tactics. You gain insight into weak spots.
-
External Network Tests: Attackers target your internet-facing assets.
-
Internal Network Tests: Simulated insider threats test internal defenses.
-
Web Application Tests: Hackers exploit code flaws in apps and APIs.
-
Wireless and Mobile Tests: Focus on Wi-Fi networks and mobile apps.
-
Social Engineering: Phishing campaigns assess human vulnerabilities.
Each type delivers unique benefits. By mixing these tests, you build a robust security posture.
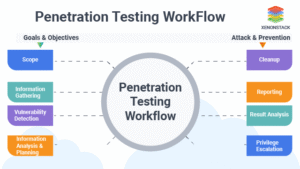
What is Penetration Testing? Five Critical Phases Explained
What is penetration testing? It unfolds in five clear phases:
-
Reconnaissance: Ethical hackers gather public and private intelligence.
-
Scanning: Tools like Nmap map active hosts and open ports.
-
Exploitation: Testers attempt to break in using known exploits.
-
Post-Exploitation: They escalate privileges to assess deeper risks.
-
Reporting: A detailed report ranks findings and recommends fixes.
This structured approach ensures no stone remains unturned. It also aligns with standards such as PCI DSS and ISO 27001.
Complete Guide to Penetration Testing for Businesses (1 Pillar Article)
Why Your Business Needs Penetration Testing
Cyberattacks cost businesses an average of $4.35 million per breach. You cannot afford complacency. Regular pentesting helps you:
-
Prevent Data Breaches: Identify weak points before criminals find them.
-
Demonstrate Due Diligence: Show regulators you take security seriously.
-
Enhance Customer Trust: Prove you protect sensitive data.
-
Optimize Security Spend: Focus resources on real, high-risk issues.
-
Improve Incident Response: Practice reactions in a safe environment.

Why your business need penetrating testing
Many organizations confuse vulnerability scans with penetration tests. To learn more about a systematic vulnerability scan, check our vulnerability assessment service.
What is Penetration Testing? Top Benefits for Your Company
What is penetration testing? It delivers measurable ROI:
-
Risk Reduction: Lower the chance of costly, reputation-damaging hacks.
-
Compliance Alignment: Meet PCI DSS, HIPAA, GDPR, and other mandates.
-
Proactive Defense: Shift from reactive to proactive security.
-
Technical Insights: Gain deep understanding of your infrastructure.
-
Continuous Improvement: Use test results to strengthen policies and controls.
Investing in pentesting is investing in peace of mind.
Integrating Penetration Testing with Your Security Strategy
Start by defining clear objectives. Decide scope, rules of engagement, and timeline. Partner with a certified provider. Look for certifications like OSCP or CREST. Your testing cadence should reflect your risk profile—quarterly, bi-annual, or pre-launch for critical assets.
Tools can automate parts of the process, but human expertise remains key. Modern AI-driven tools speed up reconnaissance and exploitation. However, skilled professionals interpret results and guide remediation.
What is Penetration Testing? Best Practices to Maximize Value
To get the most from your tests:
-
Scope Thoroughly: Include all critical systems and apps.
-
Use Realistic Scenarios: Replicate the tactics of actual adversaries.
-
Communicate Early: Align security, IT, and executive teams.
-
Prioritize Fixes: Address high-risk vulnerabilities first.
-
Retest After Remediation: Confirm fixes work and no new issues arise.
A well-executed pentest becomes a catalyst for stronger security culture.
Choosing the Right Penetration Testing Partner
Not all providers deliver equal results. When selecting a partner, evaluate:
-
Certifications and Reputation: Look for OSCP, CEH, CISSP, or CREST.
-
Industry Experience: Seek expertise in your vertical (finance, healthcare, etc.).
-
Reporting Quality: Reports must be clear, actionable, and risk-ranked.
-
Post-Test Support: Ensure guidance for remediation and retesting.
A great partner becomes an extension of your security team.
What is Penetration Testing? External Resources for Deeper Learning
For deeper insight into pentesting methodologies, explore these authoritative sources:
-
Cloudflare’s guide on penetration testing: What is Penetration Testing?
-
SANS Institute whitepapers: Penetration Testing
-
NIST’s Risk Management Framework: Special Publication.
- Vulnerability-assessment
These resources reinforce best practices and advance your understanding.
Conclusion
What is penetration testing? It is your proactive shield against evolving threats. By simulating real attacks, you uncover and fix hidden gaps. These efforts reduce risk, support compliance, and build stakeholder confidence.
Ready to safeguard your organization? Partner with Hire a Hacker Expert for expert penetration testing services. Our certified team customizes each engagement to your needs. Don’t wait for a breach—secure your future today.



No responses yet